Zero trust security helps safeguard your business against today's mounting cyber-attacks and security challenges. Through continuous authentication and validation of user identity, zero trust security eliminates implicit trust to ensure only authorized users gain access to data, resources, and networks.
Zero Trust Security Myths You Shouldn’t Believe
Here’s How to Establish a Zero-trust Cybersecurity Strategy for Your Small Business
Spartanburg County Hit by Ransomware Attack: Lessons Learned for Businesses and Governments
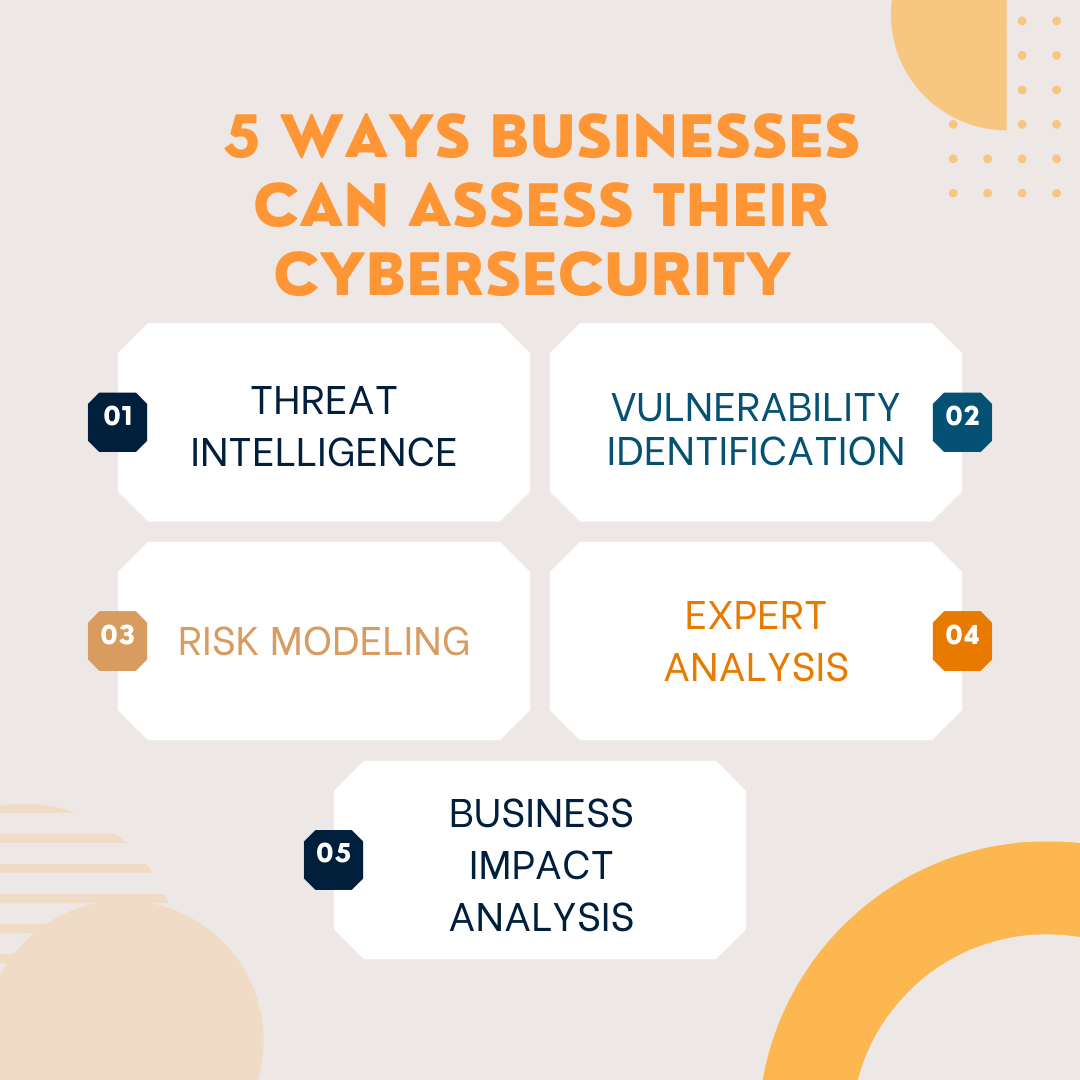
5 Ways Businesses Can Assess Their Cybersecurity
Why Outsource your Cybersecurity?

In safeguarding your business against cyberattacks, using appropriate tools and technology is only a portion of the solution.
It's equally important to possess the expertise, controls, and processes to manage and minimize these threats effectively.
This is where a Managed Security Service Provider (MSSP) comes into play.
5 Types of Risks Your Cybersecurity Risk Assessment Needs to Identify

As the world becomes more digitally dependent, businesses are facing a greater need to protect their systems and data from cyber-attacks. This is where cybersecurity risk assessments come in, as they can help identify potential vulnerabilities that could lead to data breaches, ransomware attacks, and other cyber threats.
Understanding the Importance of Cybersecurity Risk Assessments

Today, risk assessment is one of the most important factors in the process of ensuring the cybersecurity of any firm. In this post, we'll go over what a risk assessment is, why it's important, and the stages involved.
So, what is a risk assessment in cybersecurity? Simply put, it means searching for, evaluating, and prioritizing potential dangers related to cybersecurity to the resources, records, and information of a business.
The Shocking Truth: How Hackers Can Infiltrate Your Email Accounts Without Your Password or Username
We have a new National Cybersecurity Strategy, what does it mean?

In this 39-page document . . .
The Biden administration starts off by recognizing that cybersecurity is here to stay, that this is something that everybody should learn to live with and do as part of their use of technology. The document also says that the administration is investing 65 billion to make sure every American has access to reliable and high-speed internet.