Running a business is like driving a high-performance car in a fast-paced race. The thrill of speed, the challenge of competition, and the unrelenting push for excellence keep you on your toes. But even the most finely tuned racecar requires regular pitstops to stay in the game.
How to Safeguard Your Business Against Cyberattacks – Insights from a Cybersecurity Expert
The Rising Tide of Cyber Attacks on US Cities – Cleveland’s Latest Ordeal
The Rising Threat of Ransomware and What It Means for Businesses
Beware Of Cybersquatters!

Have you ever searched for a specific website but landed on a completely different one after misspelling a letter or two in the URL? This deceptive tactic is known as "cybersquatting." This practice not only jeopardizes the online presence of businesses and individuals but also poses a significant challenge in the ever-evolving landscape of cyber security.
How Hackers Are Using AI to Carry Out Sophisticated Cyber Attacks

Cybercriminals are increasingly using artificial intelligence (AI) to carry out sophisticated attacks, making it increasingly challenging for businesses to defend against them. While AI has made significant advancements in recent years, revolutionizing many industries including cybersecurity, it has also become a double-edged sword.
Steps to Adopting Zero Trust Security
Spartanburg County Hit by Ransomware Attack: Lessons Learned for Businesses and Governments
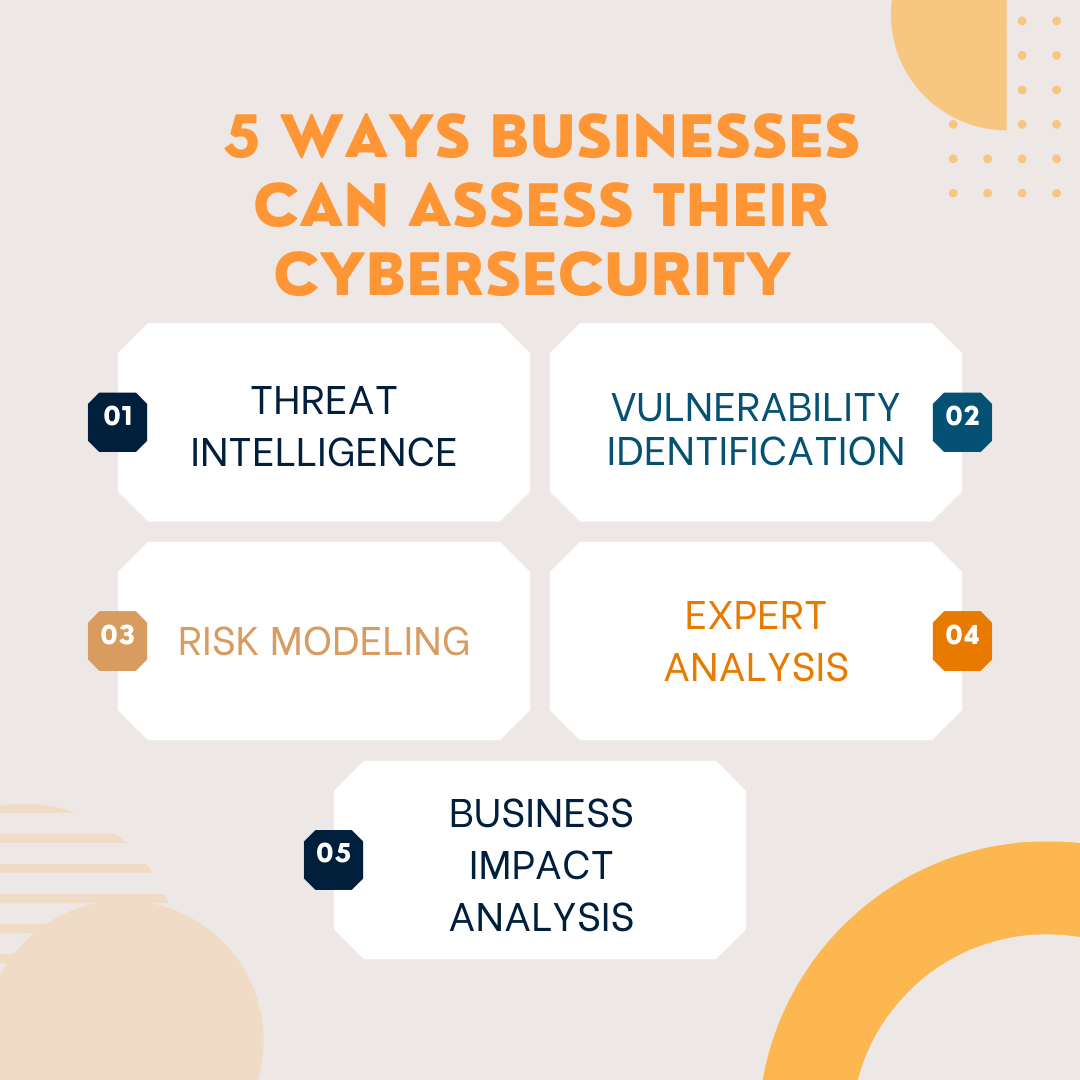
5 Ways Businesses Can Assess Their Cybersecurity
How do Cybercrimes Ruin Companies? Let’s Count the ways.
The consequences of a successful cyberattack can be catastrophic for a business, ranging from reputational damage to financial loss and even bankruptcy.
In this blog post, we'll explore the various ways that cybercrime can ruin companies, highlighting real-world examples of organizations that have fallen victim to these attacks.