 Phishing scams rank among the most pervasive and effective forms of cyberattacks. Recognizing the significant danger they present to businesses like yours is crucial. Without a clear understanding of how malicious actors exploit phishing emails, your business could easily find itself as the next victim.
Phishing scams rank among the most pervasive and effective forms of cyberattacks. Recognizing the significant danger they present to businesses like yours is crucial. Without a clear understanding of how malicious actors exploit phishing emails, your business could easily find itself as the next victim.
In this blog, you'll learn cyber criminals' motivations behind phishing emails, explore the diverse array of phishing attacks, and, most importantly, discover actionable steps to strengthen your email security and safeguard your business.
Motivations Behind Phishing Emails
Cybercriminals use phishing emails to trick employees or business owners into doing things that can harm the business. This includes sending money, giving away passwords, downloading harmful software, or sharing sensitive information. The main goal of a phishing attack is to take your money, your data, or both.
- Money Theft: The primary aim of most phishing attacks is to steal your money. Scammers employ various tactics, like Business Email Compromise (BEC), to carry out fraudulent money transfers. They may also use ransomware attacks to extort money from victims.
- Data Theft: Cybercriminals highly value your data, including usernames, passwords, identity information (e.g., social security numbers), and financial details (e.g., credit card numbers or bank account information). This data is like a treasure to them. They can use your login credentials for financial theft or inject malicious software. Your sensitive data may also be sold on the dark web for profit.
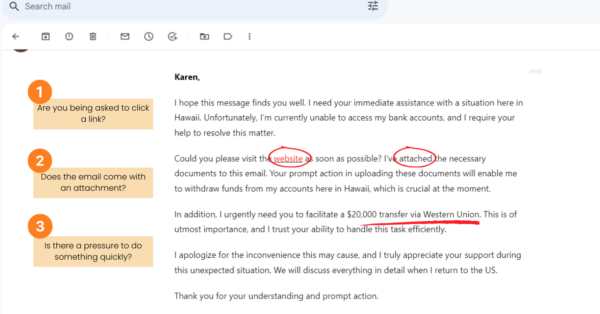
How to Spot Phishing Attempts
- Be cautious if an email asks you to click on a link. Scammers often use these links to sneak in malicious software that can swipe your data and personal info.
- Approach with care if an email tells you to visit a website. It might be a sneaky site out to snatch your personal info, like your login details.
- Stay alert when an email comes with an attachment. Those seemingly innocent files, like fake documents or invoices, can secretly infect your computer and steal your personal info.
- Is there a pressure to do something quickly? Be suspicious if an email pressures you to take quick action, like transferring money. Take a moment to double-check the request's legitimacy before you do anything.
Different Types of Phishing Attacks

Download our free eBook today to learn the different threats that plague email communication, best practices for staying safe while communicating online, and more...
It's crucial to understand that phishing attacks are continually changing and can affect businesses of all sizes. While phishing emails are a common tool used by cybercriminals, they also employ text messages, voice calls, and social media messages to deceive victims.
Here's a breakdown of the various types of phishing attacks to be vigilant against:
- Spear Phishing: Scammers send highly customized emails to individuals or businesses, aiming to convince them to share sensitive data like login credentials or credit card information. These emails may also carry malware.
- Whaling: A specialized form of spear phishing, whaling targets high-ranking executives. Perpetrators impersonate trusted sources or websites to steal information or money.
- Smishing: An increasingly popular cyberattack, smishing uses text messages that appear to be from trusted sources to persuade victims to disclose sensitive information or send money.
- Vishing: Cybercriminals use vishing (voice phishing) to impersonate entities like the IRS, banks, or the victim's workplace when making phone calls. The goal is to coax the victim into revealing sensitive personal information.
- Business Email Compromise (BEC): BEC is a type of spear phishing that employs a seemingly legitimate email address to deceive the recipient, often a senior executive. The primary aim is to convince employees to transfer money to cybercriminals under the guise of a legitimate business transaction.
- Angler Phishing: Also known as social media phishing, this scam targets social media users. Cybercriminals posing as customer service accounts trick frustrated customers into revealing sensitive data, including banking information. They often focus on financial institutions and e-commerce businesses.
- Brand Impersonation: Brand impersonation, or brand spoofing, encompasses phishing scams across various communication channels, including emails, texts, voice calls, and social media messages. Cybercriminals impersonate well-known businesses to deceive customers into divulging sensitive information. Such scams can not only harm customers but also damage a brand's reputation.
Enhance Your Email Security
Emails play a vital role in your business's success. Yet, ensuring email security and adhering to best practices can be a complex task. This is where teaming up with an IT service provider like us makes sense. We possess the necessary resources and tools to shield your business from cyber threats, allowing you to concentrate on essential tasks without concerns. Reach out to us today!
In the meantime, for insights on safeguarding your inbox, download our eBook: Your Guide to Email Safety. This resource will empower you to boost your email security and steer clear of potential pitfalls.




You must be logged in to post a comment.