Today, I want to shed light on a recent cyber attack that hit a Fortune 500 Real Estate title insurance and settlement services company. It's crucial to understand what happened and who was involved, as it serves as a stark reminder of the vulnerabilities even large companies face in the ever-evolving landscape of cyber threats.
Fidelity National Financial Cyber Attack: What We Know So Far
Protecting Your Finances: Latest Cybersecurity Threat for Businesses in Philadelphia

There's a new cyber threat in town, and it's targeting banks, financial institutions, and cryptocurrency wallets in the greater Philadelphia area.
Remember the Xenomorph Android malware that caused a stir among 56 European banks last year? Well, guess what? It's back, and this time it's targeting US banks, financial institutions, and even cryptocurrency wallets.
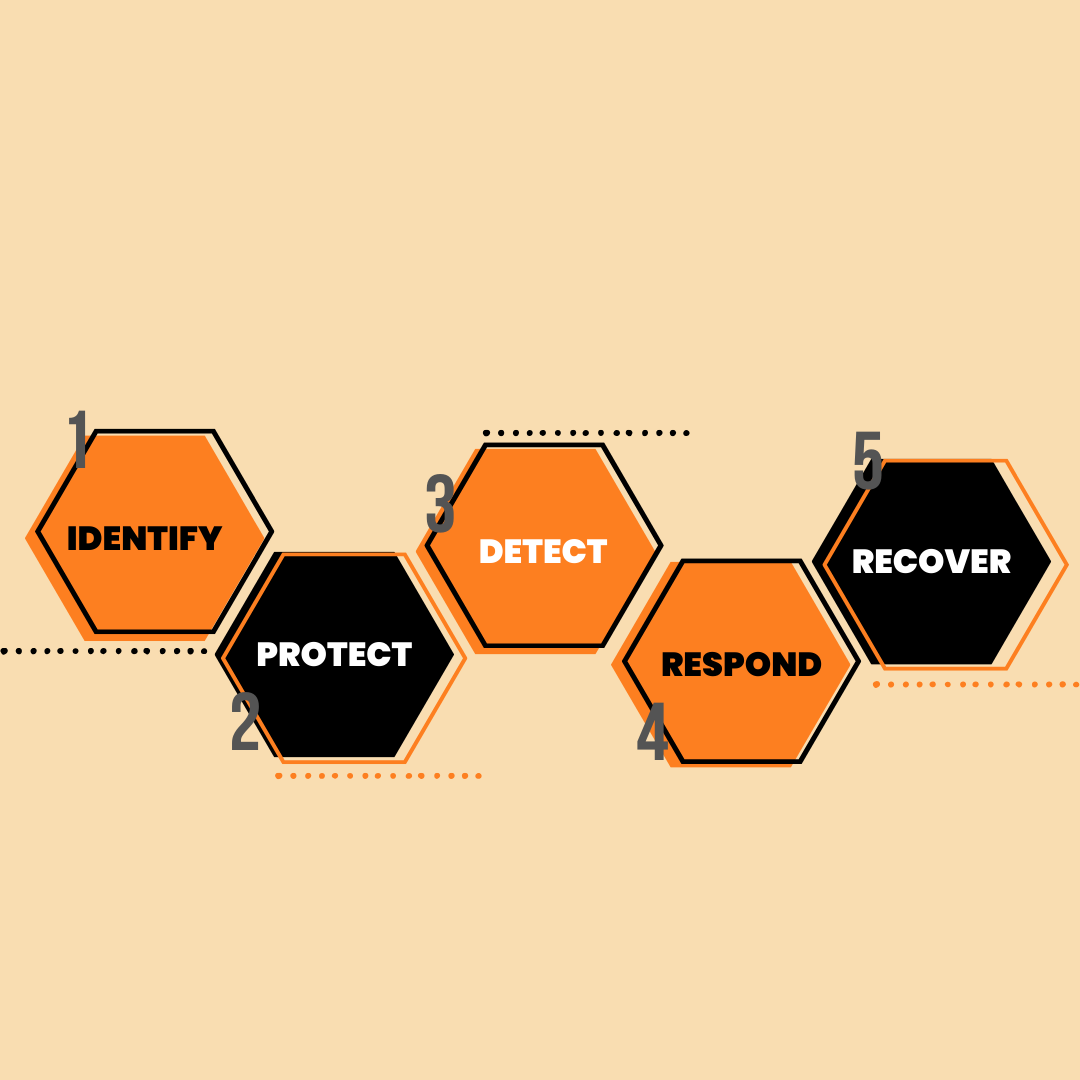
How Effectively Managing Risk Bolsters Cyber Defenses

In today’s rapidly evolving digital landscape, where cyber threats and vulnerabilities continually emerge, it’s obvious that eliminating all risks is impossible. Yet, there’s a powerful strategy that can help address your organization’s most critical security gaps, threats, and vulnerabilities — comprehensive cyber risk management.
How to Achieve Strategic Cyber Risk Management With NIST CSF
Feasting Safely: A Cybersecurity Guide for Thanksgiving Weekend
As the Thanksgiving weekend approaches, our minds are filled with thoughts of turkey, pumpkin pie, and quality time with loved ones. However, amid the festivities, it's important to remember that cybercriminals don't take holidays off like we do. Thus, it's crucial not to forget about the importance of staying cyber-safe, especially with the shopping extravaganza of Black Friday and Cyber Monday around the corner.
How To Have The Freedom To Do What You Want When You Want In Your Business

Could you step away from your business for a month, and come back and have it running and growing and profitable? What about 6 months? A year? This is every business owner’s dream, but not every business owner can achieve it.
You will have the opportunity to attend a free event where you’ll discover how to get rid of the grunt work you don’t like so you can delegate it, strategies to empower your team to do more so you can focus your time on becoming more profitable, and the steps to take now so you can go on that monthlong vacation in the near future.
Top Technologies Driving Digital Transformation

When creating your business budget, don't just see technology costs as operational expenses—view them as investments propelling your organization toward unprecedented productivity, growth, and profitability.
Ditch the mundane numbers and spreadsheets; embrace a budgeting process that shapes your business's future.
Top Digital Transformation Myths Debunked

In the fast-paced landscape of today's business world, digital transformation stands out as a crucial element for success. Its potential to attract new customers, enhance efficiency, and boost profits is undeniable. Despite these benefits, numerous misconceptions often deter business owners from embracing the digital revolution.
Siri Co-Founder To Reveal The Coming AI Revolution And How To Harness It
Navigating the Fallout: Mr. Cooper’s Cyber Attack

On the eerie night of Halloween, instead of the expected scares and pranks, Mr. Cooper found itself plunged into a real-life nightmare—a massive cyber attack that disrupted its systems and operations. In this blog post, we'll delve into the implications of this cyber attack on Mr. Cooper's millions of customers.